TL;DR – how to
Yes, you do. In order to do that you’ve to generate an RSA key with
$ openssl genrsa -aes256 -out private-key.pem 2048
and, when prompted, enter a passphrase for encrypting the private key.
$ openssl req -new -x509 -days 3650 -extensions v3_ca -key private-key.pem -out certificate.pem
and, when prompted, type the password you choose before. Then, follow the wizard by answering the questions which will be prompted.
Now you should have two files: certificate.pem and private-key.pem
- certificate.pem is a standard x509 binary certificate that’s valid for 3650 days
- private-key.pem is an RSA key (AES-256) used to encrypt the certificate
OPT: if you want to add this certificate on Windows computers via GPO you should create a .pfx file which is commonly used to bundle a private key with its X.509 certificate or to bundle all the members of a chain of trust – more info here
$ openssl pkcs12 -export -out windows-certificate.pfx -inkey private-key.pem -in certificate.pem
In order to distribuite the certificate to all your computers you can create a new GPO on your Domain Controller and go to: Computer Configuration > Windows Settings > Security Settings > Public Key Policies and finally right click “Trusted Root Certification Authorities” and import the .pfx file created.
Finally assign the policy to your Organization Unit.
Last step, import the certificate on your firewall and enable the DPI function for outgoing traffic.
Now it’s time to go deeper.
What is SSL Inspection?
SSL inspection is a tecnique about intercepting and reviewing encrypted internet communication between client and server. The inspection of SSL traffic has become critically important as the vast majority of internet traffic is SSL encrypted, including malicious content.
How does SSL Inspection work?
To put it in simple terms, SSL Inspection is a man-in-the-middle attack executed to filter out malicious content. SSL Inspection is done by an interception device. This interceptor sits in between the client and server, with all the traffic passing through it.
When the connection is made over HTTPS, the inspector intercepts all traffic, decrypts it and scans it. First, the interceptor establishes an SSL connection with the web server. Here, it decrypts and examines the data. Once the scanning is done, it creates another SSL connection—this time with the client (browser). This way, the data gets to the client in an encrypted format—the way it was intended originally.
On the Fortinet documentation there is a very well done diagram which can help to understand better the data flow.
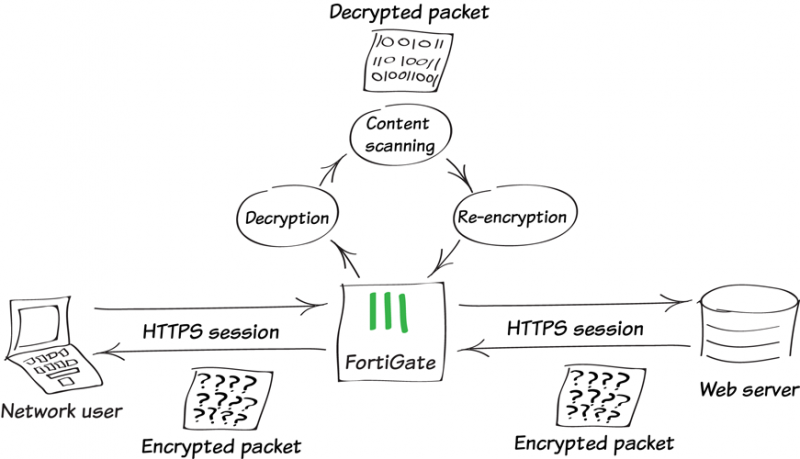
What is used for?
SSL inspection improve an organization’s web security like application identification, URL filtering enforcement and malicious content filtering. When deploying an NGFW for HTTPS inspection, normally I suggest to implement the following best practices:
- Inbound vs Outbound Inspection: Inbound inspection looks at traffic flowing to the client, while outbound inspection monitors traffic to the server. Inbound inspection can protect internal webservers by applying IPS (Intrusion Prevention System) protections.
- Respect Legitimate Privacy Concerns: Some types of data are protected under regulations like GDPR, PCI DSS, and HIPAA. The HTTPS inspection rules should be configured to ignore traffic likely to contain these types of sensitive data (i.e. to financial institutions, healthcare organizations, etc.).
- Recommended Bypass List: HTTPS inspection increases network latency and is unnecessary for certain trusted sites. An NGFW should have the ability to use an updateable bypass list to determine which traffic should not be inspected.
- Gateway Certificate: Import the gateway certificate so the endpoint browser will trust the security gateway certificate. This is essential for eliminating browser warnings and creating a seamless user experience.
Final considerations
So, do I need SSL inspection?
Yes, but don’t overdo it.
Abusing this system could cause quite a few false positives.
My advice is to implement it little by little and always respecting the points highlighted in the previous paragraph.
EOF